Table of Contents
Linux training for beginners
| Project owner: | Overdrive |
| Interested: | Filuta, Rado808,Cyberian, MiM |
| Related: | GitHub - Labka Repo : Secretary scripts – GitHub : Over's IRSSI config - comment-less – Par zakladu Linuxovych commandu - vyhodit SSH heslo a nastavit klice, SCP, tar.gz a podobne – zajimave vychytavky pro terminal |
| Linkz: | |
| Training materials - README | us/pw: student:student1 |
| https://www.xquartz.org/ | w11 pro mac |
| http://www.geo.mtu.edu/geoschem/docs/putty_install.html | X11 forward s PUTTY a XMING |
| https://mobaxterm.mobatek.net/ | nahrada PUTTY s vlastnim X serverem, MUSH, telnetem a hromadou vychytavek |
| License: | Uveďte původ-Zachovejte licenci CC BY-SA |
Lession 1 + 2 : Topics to teach and work on : TOTAL BASICS
- create USB with some linux distro from windows [later from *NIX] by https://www.linuxliveusb.com/
- connect 4 RPI [PICKY] to wiifi and nmap it [cyberian]
- get back password because we do not know cluster SD card config [cyberian]
- create user account on machine darkstar for all users [they must be able to generate secure a pub key and connect by it to server]
- next step, same it will be on PICKY [Filuta]
- turn off connection by username [google it]
- add user to sudoers [visudo or wheel] - not lame on darkstar [google it, to explain su, sudo and root]
- show them basic of IRC [hex chat for GUI a IRSSI on tmux]
- explain user rights
- explain pipes and > and »
- explain directory structure
- explain tmux/screen and why
- show them how to google problems
- configure idiotic cinnamon to react to single click to copy and paste
- find how to DDC Send and DDC Accept file over IRC
- naucit je poznat verzi kernelu a verzi systemu
- ukazat, proc je dobre si zmenit nastaveni bashe PS1 generator bash PS1 promenne, nacpat do ~/.bashrc
- naucit pouzivat man, less, heledani, zaklady vim/vi, tar.gzip, scp, mount, roury, grep, find
Lession 1 : worknotes
MiM
IRC DCC send and accept file:
- send ToDo.txt to Secretary
/dcc send Secretary /home/over/ToDo.txt
- secretary acceptuje ToDo.txt od Over23
/dcc get Over23 ToDo.txt
- muzu konnection upplne odmitnout
/dcc close get nick file“
Filuta
* Takhle nejak je spravne generovani klicu
na serveru kam se chceme dostat
mkdir ~/.ssh chmod 700 ~/.ssh touch ~/.ssh/authorized_keys chmod 600 ~/.ssh/authorized_keys
na lokalni masine, ze ktere na ten server lezem
- vygeneruje klic s emailem over@labka.cz uvnitr; format sifry bude dsa
over@SemTex ~> ssh-keygen -t dsa -C "over@labka.cz"
- tady vidis, jak Ti vyrabi 2 soubory id_dsa, to je soukromy, ten se z ruky nedava, a id_dsa.pub, ten muzes treba poslat po irc nebo emailem nebo po chatu adminovy serveru, aby Ti jej pridal do '~/.ssh/authorized keys'
Generating public/private dsa key pair. Enter file in which to save the key (/Users/over/.ssh/id_dsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /Users/over/.ssh/id_dsa. Your public key has been saved in /Users/over/.ssh/id_dsa.pub. The key fingerprint is: SHA256:7+ZxyiHPi5n5cUCDbqe/5D8Vd2Uc7mM2fWAoBN7rVxA over@labka.cz The key's randomart image is: +---[DSA 1024]----+ | ... E o.| | . + o. +| | o = o oo.| | . . + oo.+| | S + .O+| | . = . .+ +| | o B +. | | #.O. | | =+&+.. | +----[SHA256]-----+
porad na lokalni masine, ze ktere na ten server lezem
- tady delam trosku magic, viz man 'ssh-copy-id'; ktery umi vzit soubor s .pub kicem, kterej mu reknes za parametrem -i a zkopirujeho na user@server [v mem pripade tedy over@labka]
- aby tohle fungovalo, musi se na ten server nekdo byt schopen vzdalene dostat, proste over uz tam kic mit musi, nebo musi byt schopen se prihlasit heslem
- dalsi moznost je proste ta, ze mi posles *.pub soubor emailem, a ja jej dam na spravne misto
over@SemTex ~> ssh-copy-id -i /Users/over/.ssh/id_dsa.pub over@labka /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/Users/over/.ssh/id_dsa.pub" /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'over@labka'" and check to make sure that only the key(s) you wanted were added.
jinak kde byl zakopany pes a proc se to furt nechtelo prihlasit klicem...
na lokalni masine, ze ktere na ten server lezem [jmenuje se jinak nez darkstar] * spravne jsi si vygeneroval klic
ssh-keygen -t rsa -C "filuta.cz@gmail.com"
* ale poslal jsi mi jej blbe…. ecfds-sha3-mistp256 ma byt na stejnem radku jako zbtek retezce jen oddeleny mezerou; to vzniklo asi nejakym pitomim copy pastem, do priste najdem nejake mozne nastaveni jak spravne copy-pastovat nebo zkusime jina okynka
- takze ne takhle
ecdsa-sha3-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJKjKbRMNEIvBbjx/6PLq90X35uWAvWW2z36+E8SHB64eQ2EBqi6OISyxc9QXFsHlQx059ntwIE+CCdO6cPf7HM= filuta.cz@gmail.com
- ale takhle jo
ecdsa-sha3-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJKjKbRMNEIvBbjx/6PLq90X35uWAvWW2z36+E8SHB64eQ2EBqi6OISyxc9QXFsHlQx059ntwIE+CCdO6cPf7HM= filuta.cz@gmail.com
- posledni vymrd, proc Ti to nefunguvalo bylo to, ze kdyz nekdo [asi ja] vytvarel adresar a podadresare '/home/filuta/.ssh' patrili rootovi, poznal bys to takze bys napsal 'ls -la /home/filuta/' a ono by Ti to napsalo neco takovehohle [ vidis, ze pre .ssh je dvakrat napsano root root? to znamena, ze majitel souboru je root, a groupa, ktere soubor taky patri, je taky root; jenze protoze mame prava drwx——; je to vlastne hrozne blbe… pac prava d = je to adresar; r - pravo cist, w - pravo psat, x - pravo spustit [u adresare i listovat]…. jenze, kdo to muze delat? drvx——; znamena, ze tyhle prava ma jen 'root' pac je vlastnik, a prava rvx jsou nastavena jen pro vlastnika; kdyz by byla prava treba d——rwx; tak uz by to fungovalo, pac prvni rvx jsou pro usera, druhe rwx = pro skupinu [ktera tady je taky root, to by nam moc nepomohlo] a treti rwx - je nebezpecne jakxsvine, znamena to, ze k tomuhle souboru bude moct pristupovat kazdej a delat s nim cokoliv.
na serveru kam lezem [jmenuje se darkstar]
[root@darkstar filuta]# pwd /home/filuta [root@darkstar filuta]# ls -la total 28 drwx------ 4 filuta filuta 136 Jul 14 04:23 . drwxr-xr-x. 19 root root 4096 Jul 13 19:35 .. -rw------- 1 filuta filuta 13 Jul 14 04:23 .bash_history -rw-r--r-- 1 filuta filuta 18 Oct 30 2018 .bash_logout -rw-r--r-- 1 filuta filuta 193 Oct 30 2018 .bash_profile -rw-r--r-- 1 filuta filuta 231 Oct 30 2018 .bashrc -rw-r--r-- 1 filuta filuta 334 Oct 30 2018 .emacs drwxr-xr-x 4 filuta filuta 37 Mar 28 2017 .mozilla drwx------ 2 root root 28 Jul 14 04:32 .ssh -rw------- 1 filuta filuta 66 Jul 14 04:18 .Xauthority <code> * logickym resenim bylo tedy opravit vlastnika souboru, aby pouze vlastnik mel pravo 'rwx' a nikdo dalsi, ale aby vlastnikem byl 'filuta' * to udelame pomoci pripazu chown = change owner; a chgrp = change group [jeste nakonci ukazu, jak se muzes optat, kdyz nevis, jake commandy se k necemu pouzivaji, k tomu se taky dostanem] * nejdriv si opravim ownera, coz se dela commandem 'chown', pouziji jej s parametrem '-R', coz znamena rekurzi, tedy i vsechny soubory v adresari, ktery opravuji budou patrit filutovi; vsimni si, ze to musim delat jako root, protoze nikdo jiny nema prava se souborem manipulovat; zatim <code> [root@darkstar filuta]# chown -R filuta /home/filuta/.ssh/ [root@darkstar filuta]# ls -la | grep ssh drwx------ 2 filuta root 28 Jul 14 04:32 .ssh
- tady jsem si zas udelal dlouhy vypis infa o souboru [kdyztak co to umi se dozvis zase 'man ls']
- zaroven jsem pouzil tak zvanou pipe, takove to, co vypada jako I, aleve skutecnosti je to tohle '|'
- to zpusobilo, ze vypis ls -la, ktery by jinak byl docela dlouhy, to poslalo do specialniho filtru, kteremu jsem rekl, at mi vypisuje jen radky na kterych je jen konkretni slovo, v tomhle pripade ssh; nemusis jej tam psat cele nebo s nejakejma hvezdickama, jako ve widlich, i kdyz i to se da a budem se to ucit, ale pozor, cely Linux je case sensitive, takze Pica a pIca jsou dve jina slova… pokud by si si nebyl jisty, jak grep pouzit tak, aby hledal i radky se SSh i ssh i treba sSH, pouzil bys parametr '-i', ktery rika, kasli na velka a mala pismena, nekdy je to dobry, jindy ne [-i = insensitive, -R = recursive, -v = verbose …. casem zjistis, ze parametry commandy jsou vicemene furt podobne, vzdycky jdou najit 'prikaz –help'; nebo 'man prikaz'.
- o pajpach a filtrech budem jeste mluvit, je to nejdulezitejsi vychytavka linuxu vubec
- tady jsem si jen z legrace vyrobil soubor .SsH, abych Ti ukazal grep s '-i' a bez nej
- soubor .ssh uz tam samozrejme je, ten jsme predchvili menili a vsecko
[root@darkstar filuta]# touch .SsH
- vidis, bez '-i' vidis jen to, co jsi napsal za grep, tedy 'ssh', vsecko malejma
[root@darkstar filuta]# ls -la | grep ssh drwx------ 2 filuta root 28 Jul 14 04:32 .ssh
- tady uz je to lepsi a vidis i soubor '.SsH'; ktery rovnou smazem, pac jej tam stejne nechcem, byl jen na ukazku [mmmchodem, delal jsem jej zase jako user root, takze zas ma majitele a skupinu root], a porad mame jeste puvodni problem, ze i normalni '.ssh' nema jeste dobre skupinu, ktera nema byt 'root' ale starej dobrej 'filuta'
[root@darkstar filuta]# ls -la | grep -i ssh drwx------ 2 filuta root 28 Jul 14 04:32 .ssh -rw-r--r-- 1 root root 0 Jul 14 05:05 .SsH
* tak si teda promaznem .SsH, pac je k nicemu, pouzil jsem '-v' tedy ukecanou verzi prikazu, a '-R' coz je zase rekurze, tedy smazal by i adresar a vsechno co se v nem nachazi... na tyhle prikazy HODNE bacha, jednou neco smazes jako root, tak je to smazany
[root@darkstar filuta]# rm -Rv .SsH rm: remove regular empty file ‘.SsH’? y removed ‘.SsH’ [root@darkstar filuta]# ls -la |grep -i ssh drwx------ 2 filuta root 28 Jul 14 04:32 .ssh
* tak jo, tak jsme si jeste zmenili '-R' tedy rekurzivne pomoci 'chgrp' = tedy change group groupu souboru z root na filuta a otestovali jsme si ze ted vidime jen .ssh, ne zadny jiny patvara, a ten ma prava drvw------ tedy user a nikdo jiny s nim muze manipulovat [a je to d = directory]; a tim majitelem je schodou okolnosti filuta...
[root@darkstar filuta]# chgrp -R filuta /home/filuta/.ssh/ [root@darkstar filuta]# ls -la |grep -i ssh drwx------ 2 filuta filuta 28 Jul 14 04:32 .ssh
* na serveru odkud se na darkstar chcem pripojit je jeste dobry mit bookmarky na servery, kdo si ma ty stovky IP furt pamatovat
- vyrobim soubor
over@SemTex ~> touch ~/.ssh/config
* zmenim mu prava tak, aby nemel execute [jak se meni prava je dobre si nacit, budem se to ucit], kazdopadne tady mu davam jen prava pro cteni a pro psani
over@SemTex ~> chmod 600 ~/.ssh/config
- coz si zkontroluju, stejne, jako ze jej muzu pouzivat, pac jsem user over na masine SemTex, a majitel souboru,ktery do nej muze psat je nejakej over, asi je to v poradku
over@SemTex ~/.ssh> ls -la | grep -i config -rw------- 1 over staff 724 May 3 2018 config
* pomoci editoru nano nebo vim zkopiruj do souboru '~/.ssh/config' plus minus tohlencto
# jak se bude bookmark jmenovat
Host labka
# misto [SOME USER PICO] napises v tvem pripade 'filuta'
user [SOME USER PICO]
# kam te tenhle bookmark bude pripojovat.... darkstar ma ip 193.84.207.21
hostname 193.84.207.21
# tady rikas, ze by se Ti docela hodilo, kdyz by na darkstaru nahodou bezely okynka, aby sis je mohl zobrazovat u sebe, v linuxu na to nepotrebujes nic navic na macu: https://www.xquartz.org/ nebo na widlich: https://sourceforge.net/projects/xming/
ForwardX11 yes
# tohle je spis pro cyberiana, kterej porad touzil mit nekde jinde a nejak jinak pojmenovanej soukromej klic [tedy druhou pulku k tomu id_dsa.pub, tedy id_dsa
# IdentityFile /home/over/ssh_tmp/id_rsa_na_jine_misto
# taky zatim pryc, ale ssh daemon normalne posloucha na portu 22, kdyz by posouchal na nejakym jinym, takhle se to rekne
# Port 2222
- celkovy vysledek tohohle bookmarku bude, ze nebudes muset psat
ssh filuta@193.84.207.21 -p 2222 -i /home/over/ssh_tmp/id_rsa_na_jine_misto -X
- misto toho napises
ssh labka
- a tohle se stane
adelajka@Punch:~$ ssh labka Last login: Sun Jul 14 04:18:57 2019 from 88.88.88.90 [filuta@darkstar ~]$
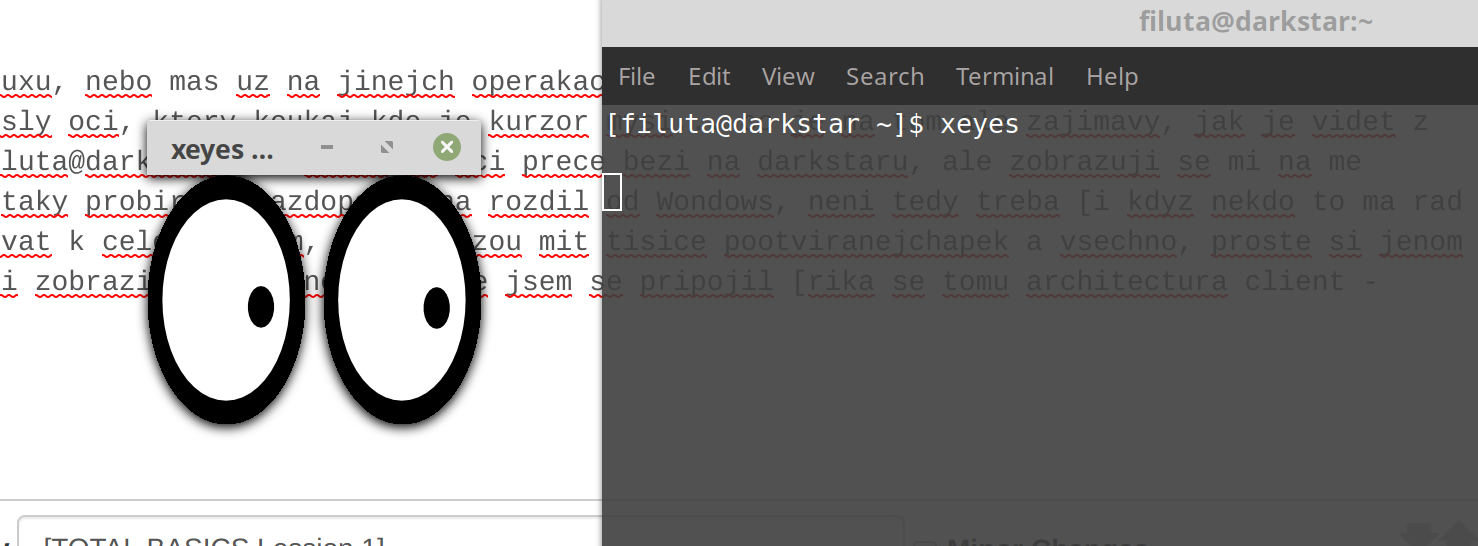
* no a dik tomu, ze se pripojujes s linuxu, nebo mas uz na jinejch operakach ootahany ty quartzi a mingy, tak kdyz spustis 'xeyes', coz je jen command, ktery nakresly oci, ktery koukaj kde je kurzor mysi… co je na tom ale zajimavy, jak je videt z uvodu commandu [tak zvaneho promptu] [filuta@darkstar]$ = takze ty oci prece bezi na darkstaru, ale zobrazuji se mi na me plose, jak je to mozne? magic. budem to taky probirat. kazdopadne na rozdil od Wondows, neni tedy treba [i kdyz nekdo to ma rad a pak se pouzivaji VMC tooly] se pripojovat k celejm oknum, ktery muzou mit tisice pootviranejchapek a vsechno, proste si jenom pustim appku, kterou chci, a necham si ji zobrazit na masine, z ktere jsem se pripojil [rika se tomu architectura client - server]
[filuta@darkstar ~]$ xeyes
Rado808
- Install software:
aptitude search neco-co-hledam aptitude install neco-co-chci-installit
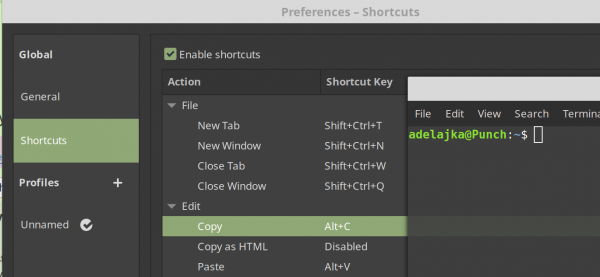
- jak premapovat shift + ctrl + c a shit+ctrl+v v terminalu na neco normalnejsiho
- v horni liste terminalu do “Edit” → “Preferences”
- celosystemove jsem to zatim jeste nenasel
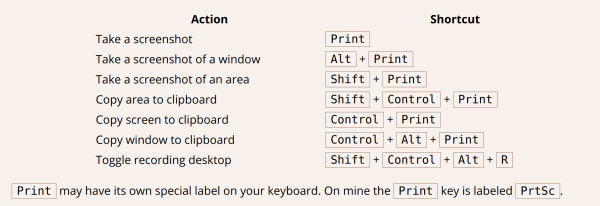
- klavesove zkratky v Linux Minutu na screenshoty [na ebu je jeste klavesovka na nahravani obrazovky, ale stejne bez zvuku]
Cyberian
THEORY :: Hack password ON rpi we do have SD card but we do not know user and pwd * Power down and pull the SD card out from your Pi and put it into your computer. * Open the file 'cmdline.txt' and add 'init=/bin/sh' to the end. This will cause the machine to boot to single user mode. * Put the SD card back in the Pi and boot. * When the prompt comes up, type 'su' to log in as root (no password needed). * Type “passwd pi” and then follow the prompts to enter a new password. * Shut the machine down, then pull the card again and put the cmdline.txt file back the way it was by removing the 'init=/bin/sh' bit.
REAL LIFE:
- 'init=/bin/sh' in 'cmdline.txt' does not work, add
systemd.unit=emergency.target
- Cant write with wireless keyboard. Switched to classical USB.
- to change password you need to remount '/' as read-write not read-only
mount -o remount, rw /
sudo passwd root Used password: **dexGauner**
* erased 'init=bin/sh' and 'systemd.unit=emergency.target' from cmdline.txt. * Applied to all four RPI
note: * instead : https://raspberrypi.stackexchange.com/questions/85146/resseting-password-using-init-bin-sh-keyboard-doesnt-work
systemd.unit=emergency.target
REMOVE - REFORMAT - REDO
DO NOT MESS USER RIGHTS OF FILES AND DIRS
mkdir ~/.ssh chmod 700 ~/.ssh touch ~/.ssh/authorized_keys chmod 600 ~/.ssh/authorized_keys
example of generating key to non standard position
over@darkstar>mkdir ~/ssh_tmp ssh-keygen -t rsa -C "tpetru@gmail.com" -f ~/ssh_tmp/id_rsa_na_jine_misto Generating public/private rsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/over/ssh_tmp/id_rsa_na_jine_misto Your public key has been saved in /home/over/ssh_tmp/id_rsa_na_jine_misto.pub. The key fingerprint is: SHA256:hriECJShFg+8AKVHVkoqYtBknvhf/sGW+KQr4wqtEUE tpetru@gmail.com The key's randomart image is: +---[RSA 2048]----+ |=EX.. | |*%=o | |@o*. | |** . . . | |o o o o S | | o o + + . | |o . o o * | | + o * . | |. .o.oo.o | +----[SHA256]-----+
create ~/.ssh/config for labka
touch ~/.ssh/config chmod 600 ~/.ssh/config
* add there this block of code; user needs to be correctly set up:
Host labka
user [SOME USER PICO] # here your server user must be configured
hostname 193.84.207.21 # ip of LABLA Darkstar in this case
ForwardX11 yes #forward windows from Linux server to local machine
IdentityFile /home/over/ssh_tmp/id_rsa_na_jine_misto # because strange generatated in previous steps
* next time, you can connect to server by
ssh labka
instead of
ssh [some_user]@193.84.207.21
MOAR RELATED LINKS : Linux from command line
NSH [network shell]
NSH basics for BSA automation:
nexec -i -e su